Monday, December 22: The Scribbler
TALES FROM THE CRYPTANALYST
by James Lincoln Warren
Stories featuring codes and ciphers represent an entire subgenre of mystery. The first such story ever written was, of course, by Edgar Allan Poe, “The Gold Bug”. It served to inspire another classic, “The Adventure of the Dancing Men”, by Arthur Conan Doyle. Among sleuths who had a talent for deciphering coded messages, none were as clever, I think, as Dorothy L. Sayers’ Lord Peter Wimsey: among his best known decryptions were in Have His Carcase, which featured a very clever substitution cipher based on replacing letters written within a rectangle, and The Nine Tailors, which brilliantly featured a cipher based on English bell change-ringing patterns imbedded in what at first seems to be the written ravings describing a lunatic’s hallucinations.
This latter is an example of what is called steganography, a secret message so designed to hide the fact that it even contains a secret message. There is nothing new about secret writing, of course. One of the earliest examples of a steganogram is the early Christian symbol of the fish:
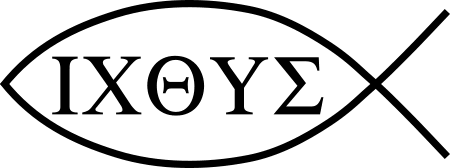
This was used in Roman times to communicate between Christians that they were adherents to the same forbidden faith. The symbol consisted of a simple line drawing of a fish, and the way it was communicated was like something out of a spy novel via sign and counter-sign. One Christian would draw the top curve, and the response was to draw the bottom curve, finishing the drawing. The resulting image was a symbol of Christianity, among other symbolic reasons because the Greek word for fish, “ichthys”, was an acronym, “I-CH-TH-Y-S”, for Iesous Christos Theos Yios Soter, which translates more or less as “Jesus Christ, Son of God, our Savior”.
Secret writing was also very common among medieval hermeticists, especially alchemists, and for several reasons. First, anybody interested in magic was seen as a heretic at a time when being perceived a heretic was not entirely healthy. Secondly, it is in the nature of hermeticists to conceal what were regarded as revelatory secrets, a tradition which goes back to pre-classical mystery cults and their initiatory rites. But sometimes, cryptography and steganography were indulged in for their own sake, and by the Renaissance, these occult arts had practical military value.
Today, of course, codes are extraordinarily sophisticated and extraordinarily difficult, if not impossible, to break, depending as they do mostly on short-lived digital manipulations computationally equivalent to “one-time pads”. The U.S. government even has an agency dedicated to covert communications, the National Security Agency, a.k.a. “The Puzzle Palace”.
These kinds of codes are useless to the mystery writer, even if they are bread and butter for thriller writers, because they are clearly beyond the capacity of any mortal detective to solve. But fear not, because there are tons of brilliant but usable ciphers available from earlier times that answer the mail.
One of my favorites, albeit non-steganographic, was invented by Blaise de Vigenère (1523 – 1596), in his 1585 book, Traicté des Chiffres ou Secrètes Manières d’Escrire (“Treatise on Ciphers or Secret Ways of Writing”). I used it in the unpublished Treviscoe novel, Whose Lust Is Murder. It is an alphabetical substitution cipher with a rotating key.1
The first thing you need is a pangram, or “holo-alphabetic sentence”, a sentence that contains all the letters of the alphabet. The quick brown fox jumps over the lazy dog. The five boxing wizards jump quickly. My girl wove six dozen plaid jackets before she quit. (A random non-repeating string of the letters of the alphabet is cryptographically superior, but not as much fun.)
In Lust, I used an excerpt from Alexander Pope’s translation of Homer’s Iliad which is actually three sentences, but wotthehell:
- The mighty Ajax shall his prize resign,
Ulysses’ spoils, or ev’n thy own be mine.
The man who suffers, loudly may complain;
And rage he may, but he shall rage in vain.
But this when time requires: It now remains
We launch a bark to plough the wat’ry plains,
And waft the sacrifice to Chrysa’s shores,
With chosen pilots, and with lab’ring oars.
Printing out each of the underlined letters in order yields the following sequence of all 26 letters:
T H E M I G Y A J X S L P R Z N U O V W B F D C Q K
(I cheated a little here. In the 18th century, “I and “J” were considered the same letter, as were “U” and “V”, but even so eminent a lexicographer as Johnson had pointed out that they really should be considered different letters.)
At this point, we draw a table using the sequence of letters along the top and sides marking ranks and columns, and fill the table with the letters of the alphabet, each successive rank offset by one letter:
T H E M I G Y A J X S L P R Z N U O V W B F D C Q K
T A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
H B C D E F G H I J K L M N O P Q R S T U V W X Y Z A
E C D E F G H I J K L M N O P Q R S T U V W X Y Z A B
M D E F G H I J K L M N O P Q R S T U V W X Y Z A B C
I E F G H I J K L M N O P Q R S T U V W X Y Z A B C D
G F G H I J K L M N O P Q R S T U V W X Y Z A B C D E
Y G H I J K L M N O P Q R S T U V W X Y Z A B C D E F
A H I J K L M N O P Q R S T U V W X Y Z A B C D E F G
J I J K L M N O P Q R S T U V W X Y Z A B C D E F G H
X J K L M N O P Q R S T U V W X Y Z A B C D E F G H I
S K L M N O P Q R S T U V W X Y Z A B C D E F G H I J
L L M N O P Q R S T U V W X Y Z A B C D E F G H I J K
P M N O P Q R S T U V W X Y Z A B C D E F G H I J K L
R N O P Q R S T U V W X Y Z A B C D E F G H I J K L M
Z O P Q R S T U V W X Y Z A B C D E F G H I J K L M N
N P Q R S T U V W X Y Z A B C D E F G H I J K L M N O
U Q R S T U V W X Y Z A B C D E F G H I J K L M N O P
O R S T U V W X Y Z A B C D E F G H I J K L M N O P Q
V S T U V W X Y Z A B C D E F G H I J K L M N O P Q R
W T U V W X Y Z A B C D E F G H I J K L M N O P Q R S
B U V W X Y Z A B C D E F G H I J K L M N O P Q R S T
F V W X Y Z A B C D E F G H I J K L M N O P Q R S T U
D W X Y Z A B C D E F G H I J K L M N O P Q R S T U V
C X Y Z A B C D E F G H I J K L M N O P Q R S T U V W
Q Y Z A B C D E F G H I J K L M N O P Q R S T U V W X
K Z A B C D E F G H I J K L M N O P Q R S T U V W X Y
We’re now ready to do some ciphering!
Let’s choose a message to encipher. How about, “Criminal Brief”?
The first thing we do is choose one letter to act as the key. Because “F” is the last letter in the message, let’s choose it, although in practice, the letter should be determined at random or by some other method. In my story, the opening key letter was determined by the date.
Go to the top of the table and choose the column headed by “F”. Go down the column until you reached the letter we are going to encrypt, in this case “C”, the first letter of our message. Moving to left, we see that the rank is headed by the letter “A”. This now becomes the first letter of our encrypted message.
Let us now use “C”, the first letter of the unencrypted message, as the key for our next letter, “R”. The corresponding rank is headed by “B”, which becomes the next letter in our encrypted message.
Using “R” as the next key yields “F” for “I”; using “I” as the next key yields “J” for “M”. Continuing the process, our encrypted message reads:
- ABFJGXLI UCFTG
The last thing we do is break up the words so they can’t be distinguished by their length. We do this by grouping the letters in fixed lengths. Choosing a length of three letters for each grouping (in the story I used five), we wind up with:
- ABF JGX LIU CFT G
Cool, huh? And because the successive keys are contained within the message (what cryptanalysts call an “autokey” feature), it’s almost impossible to break unless you already know what the message says (what cryptanalysts call a “known-text attack”). In my story, Treviscoe doesn’t know the text, but he figures out the first key and has Vigenère’s book to help him along.
If you find this a little brain-bruising, I apologize, but exercising the little grey cells now and again does have its benefits. After all, if I were as smart as my detective, I wouldn’t have so much fun writing about him.
- This is not the so-called “Vigenère Cipher” known to Lewis Carroll, which uses a repeating key and was actually invented by Giovan Battista Bellaso in 1553 and misattributed to Vigenère in the 19th century, but a much more sophisticated method using “autokey” encryption, invented by Vigenère himself. [↩]
















I love cipher stories! I am no good at creating a cipher, let alone solving one, but my favorite kind of cipher is the chronogram. There’s a Lord Peter story that involves a crossword puzzle and an O. Henry story about a carefully-worded message from an overseas reporter (whose title I can’t remember!!!), as well as Edwd. Hoch’s stories about Rand that involved ciphers.
One of the last books I read as a kid that was not intended for adults included a code. I vividly remember that this was a simple number for letter transition, and included 15 for N because N is the fifteenth letter of the alphabet. Since even I knew it wasn’t, I decided I was done with kiddy books.
Brain-bruising? How about being run over by a Mack truck? It’s probably a good thing the characters I write about think cryptology refers to those little buildings in cemeteries for those who prefer to remain above ground.